An increasing need to reduce and mitigate threats and vulnerabilities within the food manufacturing industry has led to the development of TACCP and VACCP programs. This newsletter aims to provide an overview of these programs and how they differ from HACCP.
TACCP stands for ‘Threats Assessment and Critical Control Point’. VACCP stands for ‘Vulnerability Assessment and Critical Control Points’.
Both TACCP and VACCP strategies and steps are designed to systematically reduce risk and provide corrective actions. HACCP tends to focus on the unintentional or accidental adulteration of product where as TACCP and VACCP are more focused on the intentional adulteration, TACCP is used to identify the threat of behaviourally, economically or ideologically motivated adulterations and VACCP is used to identify the vulnerable points in the supply chain which may be a threat of an economically motivated adulteration or “food fraud”.
A detailed look at TACCP and VACCP
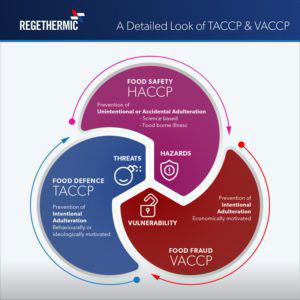
- TACCP focuses on a threat to food which may be:
- Malicious contamination of food products
- Sabotage of the supply chain
- Using food or drink items for terrorism or criminal purposes
- Economically motivated adulteration
- Extortion
- Espionage
- Counterfeiting
TACCP practically applied within a food manufacturing environment:
TACCP initiates a standard 15 stage process:
- Assess new information
- Identify and assess threats to organisation
- Identify and assess threats to operation
- Select product
- Identify and assess threats to product
- Devise flow chart of product supply chain
- Identify key staff and vulnerability chain
- Consider impacts of threats identified The TACCP Process
- Identify which supply points are more critical
- Determine if control procedures could detect the threat
- Likelihood Vs Impact = Priority
- Identify who could carry out new controls
- Decide and implement necessary controls
- Review and revise
- Monitor horizon scans and emerging risks
- VACCP focuses on the vulnerability of food and focuses on:
- The management process to defend the food supply chain from vulnerabilities due to food fraud
- Shifting the focus from risk to vulnerability
- Is based on the ‘criminological routine activity theory’.
Food fraud explained:
The GSFI (Global food safety initiative) describes food fraud as:
“A collective term encompassing the deliberate or intentional substitution, addition or misrepresentation of food, food ingredients or food packaging, labelling, product information or false or misleading statements made about a product for economic gain that could impact a customer’s health”.
Some examples of food fraud include:
- Honey diluted or replaced with corn syrup, glucose or sugar syrup
- Chalk added as a packer to flour
- Olive oil diluted with peanut oil
- Misidentification of the origin of a coffee product
- Labelled 100% orange juice diluted with other fruit juices
The chart below explains the terms used within food fraud:

VACCP practically applied within a food manufacturing environment:
- Conduct a risk analysis. Evaluate any significant risks and exposures.
- Determine the critical points for controlling the fraud.
- Determine procedures and technical means of verifying each critical point to control security.
- Determine the corrective measures to be implemented when the surveillance reveals that a critical point for fraud control is no longer under control.
- Apply verification procedures in order to confirm that the system is functioning effectively.
- Build up a file which includes all procedures and reports concerning these provisions and their implementation.
Regethermic – Equipment and solutions that promote food safety every step of the food manufacturing process
Information thanks to GSFI (the Global Food Safety initiative) and JLB

